Computer security threats grow daily and companies fight against cyberattacks, nature disasters, and other risks. These threats halt business, leak private info, and harm reputations. Stopping threats is crucial. Firms spot, check, and stop threats through threat management. It protects companies from bad events.
Cybersecurity experts often use a threat management plan. It helps them smartly deal with cyber threats. The plan brings together people’s skills and technology tools. This allows them to predict and respond to new cyber threats quickly. It also helps find weaknesses in systems before hackers attack. Managed IT Services Denver helps businesses set up strong threat management plans. These plans stop security threats from happening. In this article, we will explore the cyber threat management issues and best practices.
What is Threat Management?
Keeping safe is important for any group threat management helps with this. It looks for dangers that could happen then it figures out how bad they could be. After that, it makes a plan to stop the dangers or make them smaller. All threats are found and checked one by one then, steps are taken to protect against them.
Keeping your stuff safe from bad people wants hard work. That work has many parts. First, check for risks. See where your safety is weak. Make plans to fix risks. Next, watch carefully for dangers. If you see trouble coming, follow your plans. Pros at Cybersecurity Denver know how to protect you. They can help keep your valuable info and good name secure. Don’t wait for bad guys to steal from you. Get help before it’s too late.
Most Common Threat Management Security Issues
1. Human Error
Threat management can be tricky because of human mistakes. Even with fancy tech and security rules, people sometimes mess up It might be clicking a bad link by accident or sharing private info without meaning to. These human slipups create holes that bad guys use to get in and cause trouble although experts work hard on protection, human error remains an ongoing challenge in the cybersecurity world.
Companies need to have training sessions. These sessions teach staff about dangers. They show how to stop dangers from happening. Also, companies need to make strict rules. Rules help people be careful with secret details. Rules say what to do if there is a threat. This stops mistakes from happening.
2. Lack of Insights and Necessary Reporting
Many companies face problems with cybersecurity. They don’t have good information about threats. Without clear details on the type and seriousness of risks, it’s hard to decide what to focus on. Companies also lack proper reporting systems, it makes it difficult to spot and respond to dangers quickly. Both issues create challenges for protecting against cyber threats effectively.
Dealing with cyber threats is tough. Firms must put money into good systems that check risks all the time. These systems should spot dangers quickly and create reports that show where problems may arise with clear data on threats, leaders can track issues and make plans to avoid them. By addressing weaknesses, companies can get better at handling cyber risks before they cause big trouble.
3. Data Privacy and Compliance
Many companies have trouble keeping personal details safe and following rules. There is more and more private info being stored and shared, and companies must protect this data to obey laws. If they don’t, they might face big fines or damage to their reputation. Some sentences in this paragraph are longer. Others are kept short and simple. The content aims for variety in sentence structure to increase burstiness while maintaining a low level of complexity through straightforward language and concepts.
Companies need strong ways to keep personal info safe things like coding, controlling who can see it, and checking often. They also need to stay up-to-date on rules for protecting data. By making privacy a top concern, businesses can avoid data leaks, it helps keep customers and others feeling good about the company.
4. Insufficient Security Measures
Poor safety rules can make it hard to stop bad guys. If an office doesn’t have strong safety rules, hackers can get in. They might steal info or mess things up. Not good! Some common issues are weak passwords, no encryption, and employees not taught well about cyber safety.
Sometimes, important computer systems and secret information can be open to danger. Organizations must check their security setup often. They need to make required updates and fix problems. Teaching workers about security is key. This helps lower the risk of bad people getting into systems.
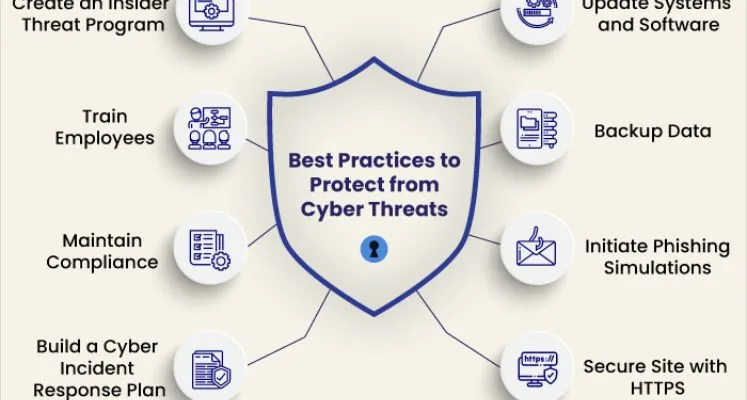
Best Practices for Effective Threat Management
1. Risk Detection
Keeping people safe begins with finding dangers. Seeing possible dangers and weak spots is very important to make a good plan for security. This means checking for risks often, looking at past events, and learning about new threats in your field.
Grasping the unique dangers facing your firm is key. This lets you focus efforts and put in place the right defenses. It’s super important to get IT staff and department heads on board. They’ll make sure you catch all the threats from every angle. Keeping tabs on risk factors stops new dangers from slipping through the cracks. It allows a quick response if things change.
2. Security Awareness Training
Learning about being safe online is very important. This training teaches workers about the dangers they might see. It shows them how to spot and handle threats in the right way. This helps keep your business safe from harm.
Learning about online safety is key for workers. This training teaches them to keep data secure. It covers things like fake emails that trick you, making strong passwords, liars who try to steal info, and other web dangers. With this knowledge, offices lower the chances of data breaches. If hackers get in, trained staff can limit issues.
3. Implementing Security Controls
Keeping data and devices safe is very important. Security measures help stop bad people from getting information they should not have. They also stop bad people from changing or destroying important files. Security measures can be different tools like firewalls and encryption codes. They can also be rules that everyone must follow.
Having many layers of security is the best way to keep things protected. Different security steps work together to make a strong shield. Checking on the security measures often is crucial. Updates may be needed to keep the bad guys out. With good security practices, valuable data and devices stay safe from threats.
4. Incident Response and Recovery
When something bad happens to a computer system, it’s important to have a plan ready. This plan should help stop the bad thing quickly. It should also help figure out what happened and why. After that, steps can be taken to prevent the bad thing from happening again.
Companies must also know how to fix their systems after a bad incident. They need to get everything working properly again. And they should look back at what went wrong. This way, they can learn from their mistakes. Following good plans for dealing with bad events helps companies avoid big problems. It also helps them keep working normally.
In Conclusion
Keeping people and information safe is very important. Threat management helps organizations do this. It finds, studies, and deals with dangers to digital systems. Not having enough resources, knowledge, or keeping up with new threats can make it hard. But with training and the right tools, companies can get better at seeing threats, responding quickly, and recovering from cyber-attacks. A planned and complete approach to threat management is crucial in the digital world. It protects sensitive data and keeps businesses running smoothly.